Cloud SASE – Identity and Access Management

SASE is a SaaS cloud cybersecurity platform that combines network and security elements to deliver a seamless secure service for various use cases.
- Zero Trust Internet Access Workplace (Office)
- Zero Trust Internet Access Remote Workforce (WFH)
- Managed Secure SD-WAN and replaces MPLS
- Decentralized Secure Internet (replace MPLS) for Remote Branches/Sites
- Ransomware Protection for the Workforce
- Secure Remote Access
- Secure Web Gateway and Web Filtering for all users accessing Internet
- Cloud Access Security Broker and SaaS Visibility
- Software Defined Perimeter and ZTNA
- FW as a Service (FWaaS)
- Cloud Application Acceleration – Cloud Fast Connect
Such functionalities are best delivered with SASE is closest to you since the medium of connectivity is the Internet. The best SASE experience is achieved by ensuring the SaaS SASE platform is located as close to the users as possible; that is where the term “edge cloud” comes in.
SASE combines numerous security frameworks, such as Zero Trust, SD-WAN, DNS security, Proxy and Web Gateway, DLP, and Firewall, on a unified cloud-based platform to provide secure network access to corporate users from any location. The significant feature is Zero Trust Access, which combines user identities through the integration of Identity Access and Management (IAM). This ensures the user’s identity is fully authenticated and authorized before access to the SASE platform is given.
Every approach that a corporate user makes to access the internet or access a corporate application from home will mean the SASE platform will first have to verify the identity of the user and ensure it has the right permission and access rights to be able to access the resource.
The concept of Zero Trust Architecture is very prominent in SASE architecture where every device and user is authenticated and authorized before access to the internet or corporate resources or workloads is given. To do this SASE platform integration with IAM platforms.
Zero Trust Architecture ensures every user, network, location, and the device is untrusted until proven. The concept is simple; trust itself is a risk. Such a concept ensures that every user and device must be validated in terms of compliance and access rights before access is authorized.
Access is restricted until your organization earns confidence by compliance with its security policies, beginning with identity verification. Unauthorized access, credential theft, and phishing may all be solved using the “trust must be earned” strategy, which also protects against identity data breaches.
IAM (Identity and Access Management) platforms such as Azure Identity Protection, Azure Active Directory and Conditional Access, Okta, Ping Identity, OneLogin, ForgeRock, and alike, will be configured to authenticate and authorize corporate users. Such a platform is known as IdP (Identity Provider) which is what the name suggests, it authenticates users and the roles or groups they belong to within an organization.
Cloud SASE platform integrates with IdP to validate the users requesting access to corporate resources or the internet. IdP is responsible to authenticate the subjects (users and devices) and providing a signal back to the SASE to permit or deny access based on the security policies configured. SASE ensures that identity security is seamless and frictionless whilst being prioritized and maintaining a positive user experience.
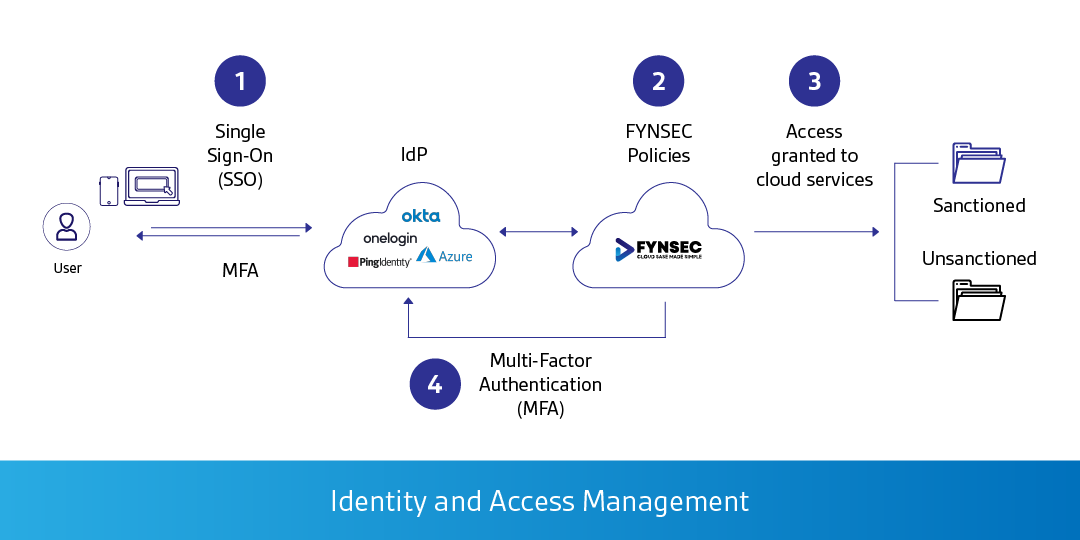
Most data breaches are triggered by compromised user credentials, insufficient authentication, authorization, lack of multi-factor authentication, and ineffective access management systems. Cloud SASE Zero Trust Identity strategy lets you quickly integrate comprehensive, time-based, context-based, and risk-based identity access management into accessing internet and corporate applications.
Every access attempt in a zero-trust identity architecture is handled as an untrusted user, an untrusted device, and an untrusted network location and is denied access unless corporate security procedures gain confidence, beginning with identity verification.
This “trust must be earned” strategy addresses security issues such as unauthorized access, phishing, and credential theft and protects against identity data breaches without interfering with the user experience of accessing corporate resources and the internet through the SASE platform.
Cloud SASE integrated with IdP simplifies workforce access by utilizing the zero-trust identity strategy whilst managing application access for an increasingly remote workforce.
- Adaptive and Risk-Based Authentication: The multi-factor authentication adapts to the user’s needs. Prevention against impersonation and credential theft utilizing adaptive multi-factor authentication (MFA) methods that is context, location, time, device, and browser fingerprint aware. Such concepts have evolved to terminologies you will hear – conditional access, risk-based access, and adaptive access.
- Frictionless with Enhanced Security: Seamless and frictionless access to resources using SSO and SAML based on Software Defined Perimeter (SDP) and Zero Trust approach. Once access is granted the authentication and authorization tokens are federated; if the device for whatever reason becomes non-compliant – access is then revoked.
Conclusion
Identity access management is essential to any organization’s success in cloud computing. Applying a zero-trust identity architecture plays a key role in the adoption of cloud services. SASE and SD-WAN services can be fully integrated and aligned towards IAM delivered through IdP.
It can increase staff productivity and organizational security by providing SSO capabilities that is advanced, risk-based, context-aware, and dynamic. Risky-logins are further scrutinized which ensures protection against credential theft and other authentication-based attacks.



