Cloud SASE – DNS Security

One of the most used network protocols is DNS (Domain Name System) – it is the lifeblood of how the Internet works. One of the critical responsibilities of the DNS server is to translate domain names into a specific IP address so that the users that requests a specific domain can fetch the requested site.
As most technological solutions were not designed with security in mind, the DNS protocol is no exception. Modern cyber threat landscape where attack techniques have increased in sophistication and are continuously evolving, the traditional cybersecurity controls in the post-pandemic era are no longer relevant with working habits changing and the need for organizations to secure users and endpoints across other locations; infrastructure that is hosted on-premises and multi-cloud environment.
DNS infrastructure are critical assets for all organizations, whether it is an enterprise or an internet or cloud service provider. Protecting DNS infrastructure from cyber-attacks is a critical activity for security professionals. Any compromise of the DNS infrastructure can result in significant ramifications. A compromise of a DNS server may result in destructive consequences both for remote and corporate users.
DNS attacks vary in complexity and nature – the context of this article is focused on the importance of DNS security for users and endpoints in the post-pandemic era where they may work from the office or remotely.
Cybercriminals have been consistently taking advantage due to mismanagement of DNS security controls within organizations to exfiltrate data out of the organization from infected endpoints and perform redirects to malicious phishing sites. DNS security is important to identify risky or dangerous domains and preventing users from connecting to them, preventing users from connecting to non-sanctioned domains where the risk of data loss is higher and identify anomalous DNS-layer activity that can indicate an infection or malicious activity.
- DNS Tunneling
- Once users are infected with malware, attackers use DNS services to bypass NGFW by tunneling protocols such as HTTP wrapped in DNS and subsequently exfiltrate data which is then reconstructed by the attacker on the receiving end.
- DNS Spoofing
- This is an attack where fabricated DNS data is injected into the memory of a DNS resolver, causing the resolution protocol to provide an erroneous IP address for a domain. Resulting in the redirecting of a legitimate website to a malicious site which may be harvesting credentials or being used to distribute malicious files.
- DNS Hijacking
- DNS Man-In-The-Middle (MITM) attack is used to redirect legitimate DNS queries to a malicious website via a hijacked DNS server. Resulting in the redirecting of a legitimate website to a malicious site which may be harvesting credentials or being used to distribute malicious files.
- NXDOMAIN Attack
- The attacker overwhelms the DNS server with a large volume of requests for records that are primarily non-existent or invalid. In most circumstances, the invalid domain results in a spray attack that is forwarded to DNS Proxy server, which consumes its computing resources by resolving to the DNS authoritative server for these invalid entries resulting in a denial-of-service.
- Phantom Domain Attack
- The attacker creates a series of ‘phantom’ domain servers that respond slowly to the requests. The resolver is subsequently bombarded with requests for these domains, causing it to get clogged while waiting for responses, resulting in sluggish performance and denial of service.
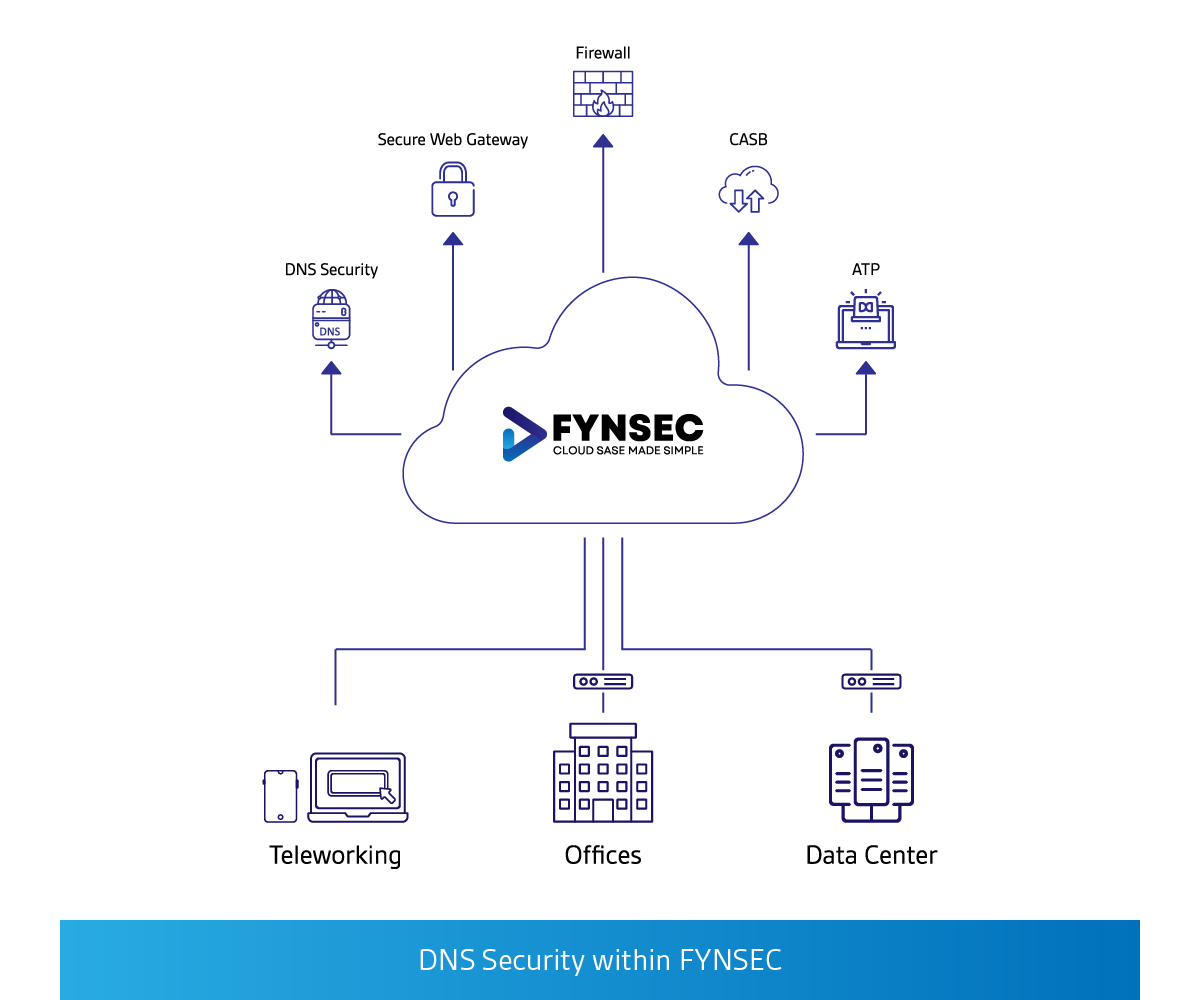
Cloud SASE (Secure Access Service Edge) delivers unrivaled Secure Internet Access for all the workforce regardless of location. Cloud SASE delivers Secure Web Gateway (SWG), Explicit Proxy, Web Filtering, Content Inspection, RBI, and CASB, with DNS Security being a vital function.
DNS security is a critical component of Cloud SASE, enabling organizations to securely access Internet resources without worrying about user browsers and devices being compromised through phishing links, redirecting users to malicious sites, or using DNS attack techniques to exfiltrate data out of the organization or
Protecting DNS layer must be considered the backbone for any organization to protect users and devices from the Internet. A primary method to prevent malicious and phishing websites being accessible and to prevent data exfiltration for compromised users.
We at FYNSEC a Cloud-Native SASE service delivers unparalleled DNS protection embedded into our service offering.
- DNS tunnelling detection and prevention
- Filters the DNS request based on domain reputation
- Botnet C&C domain blocking and redirecting to custom notification page
- Blocks the DNS request for the known botnet C&C domains
- External dynamic category domain filtering
- Define your own domain category
- DNS safe search: enforces Google, Bing, and YouTube safe addresses
- Allows you to define your own domain list to block or allow
- Allows you to define an IP block list to block resolved IPs that match this list
- Advanced DNS security analytics for anomaly detection
- DNS logging and auditing feature for CSOC



