Cloud SASE – NG-IPS and Threat Prevention

Cyber threats are getting more advanced, persistent, and sophisticated. An increase in user access connectivity to a hybrid IT environment across both corporate on-premises data centers and cloud workloads has led to security officers managing a wide attack surface to protect the organization.
An intrusion prevention system (IPS) is an advanced network and application security feature, that can detect and prevent known threats to your IT infrastructure. IPS screens your network traffic, and performs an inspection of the traffic payload from the network up to the application layers, identifying malicious payloads using known signature patterns.
Before going into the debate of IPS vs. NDR it is important to understand the historical journey of how IPS technology has evolved. IPS is signature-based and was introduced as a dedicated security appliance as the 1st generation of technology; configured in-line in the network infrastructure stack with prevention capabilities. 2nd generation of IPS was introduced as a subset feature of NGFW and UTM security appliances providing FW and IPS capabilities into a single unified security platform; however, still relies on signature-based prevention capabilities. 3rd generation of IPS has evolved to NG-IPS, which is essentially based on a hybrid approach of both signature and signature-less (using ML/AI) approach to threat detection and prevention.
NDR (Network Detection and Response) is usually coined with NG-IPS but fundamentally offers two different protection mechanisms. NG-IPS is an active appliance in line utilizing both signature and signature-less methods; relying on signature-less methods alone does not provide the defense-in-depth approach.
NDR architecture uses sensors deployed to monitor mirrored traffic across the network with an AI-brain to perform anomaly detection using cognitive and AI detection techniques. As NDR is a platform that works with mirror traffic and an offline component active response in terms of prevention is not possible unless it is integrated with active components like firewalls.
In short, NDR is not a replacement for NG-IPS or IPS as a feature in NGFW. They both complement each other. Finally knowing how payload inspection for encrypted traffic is performed is important to understand. Encrypted Traffic Analysis (ETA) is a new technique where certain support protocols look for outliers within encrypted payloads without the need to decrypt and re-encrypt traffic.
IPS can perform real-time deep packet inspection for all your network traffic, usually, IPS are placed in-line with your network traffic flow just behind the firewalls or enabled as a feature on the NGFW.
IPS can prevent cyber threats;
- Viruses and Worms
- Variety of network, transport, and application exploits
- Dos (Denial of Service) attack
- Drops malicious payloads matching REGEX patterns
- Block traffic to the targeted host by sending TCP RST flags
Signature-based detection
In this method, IPS uses well-known threat signatures to identify threats. When any new malware is detected, a new signature is generated and added to the signature list of IPS signatures. This signature database is used to match the malicious activity signature or pattern and takes preventive actions.
But this type of threat detection will only be effective against known threats and cannot prevent any zero-day attack.
Anomaly-Based Detection (NG-IPS)
The anomaly-based technique will monitor for any malicious behavior or any abnormity in your network, it creates a model for the normal behaviour of the protected resource. If IPS found any abnormality it can block access for the protected network host and generate a report accordingly.
Policy-Based Detection
A network security administrator is required to create IPS policies and profiles; keeping in mind the network and workloads being protected. IPS will report if any policy violations were detected and prevented. IPS is enabled as a function for traffic flow processing that needs to happen across a network – one example is below.
Internet > Firewall > IPS > Web Application Firewall > IPS > DMZ Server.
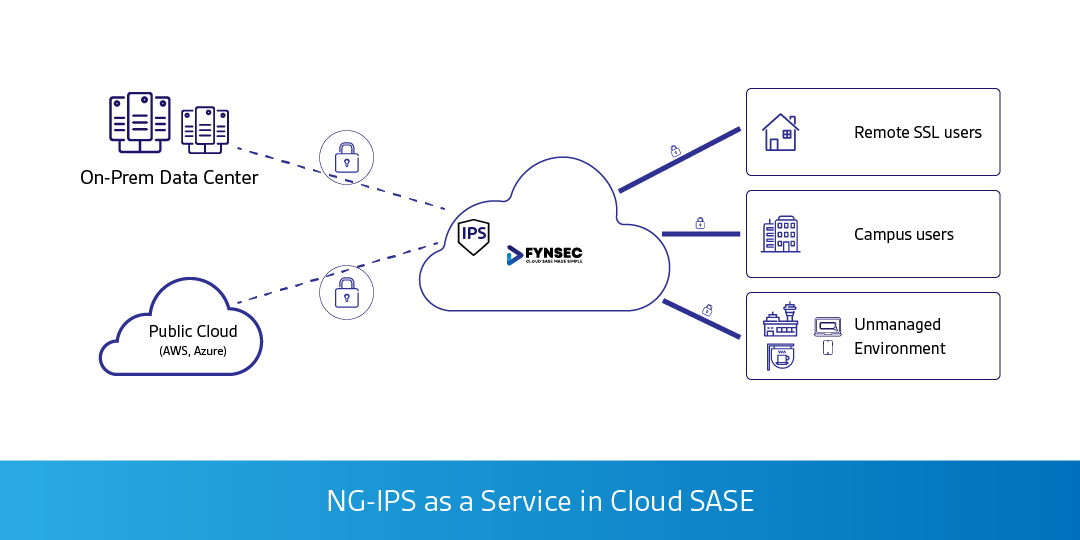
NG-IPS as a Service in your Cloud SASE is an essential security feature to ensure users browsing the Internet or accessing workloads on-premises or the cloud is protected from the network or application-borne threats and malware.
The NG-IPS includes a combination of both signature and anomaly rules that protect against known threats and vulnerabilities, whilst real-time security intelligence can track malicious payloads and anomalous behavior detection based on the traffic flow context and characteristics.
Key Benefits
Location-based On-premise solutions can face challenges, due to the limitations of corporate network design, IPS can protect traffic over network perimeters, but not for your entire network, it cannot provide protection for your mobile and cloud traffic, whilst the SASE solution can protect all possible traffic flow scenarios.
Performance is a key factor; an immense increase in your encrypted traffic can degrade performance and physical appliances that may need costly upgrades, while SASE IPS will ensure high performance in the cloud by centralizing IPS functionality for all your access needs.
Unified IPS Security Engine SASE IPS will automatically be updated with the latest signatures and anomaly detection FYNSEC Cloud-SASE IPS maintains the IPS engine updated without any need for signature-update management from security administrators, whilst providing a unified security engine through a common cloud SASE architecture for all your traffic flows.
Conclusion
IPS and NG-IPS is an essential part of modern cybersecurity control to counter advanced threats. It should not be confused with NDR which ultimately provides complimentary security protection. IPS is a subset feature and is now being offered as a Service through the Cloud SASE for all hybrid workforce and workload environments. As organizations move towards a perimeter-less architecture, the need for FW+IPS as a Service in Cloud SASE with Zero Trust Network Architecture becomes an integral part of any digital transformation strategy.
Learn more about how FYNSEC Cloud SASE can help you in this journey.



